
Atlantech Online Blog » Latest Articles

According to the latest Netscout Intelligence Threat Report, there were over 9.7 million Distributed Denial of Service (DDoS) attacks in 2021. That is 14% higher than pre-pandemic levels. As business returns to normal, we can expect to see those numbers increase, even further. The time to secure your network is now, if you haven't done so already.
DDoS attacks can strike at any time with potentially paralyzing effects to your network. Over 85% of attacks are less than 10 minutes. At a minimum, they can compromise your user/customers’ experience and reportedly often shut down networks completely, resulting in lost productivity, revenue and costly bandwidth charges. Just a cursory look at the national news reveals that these attacks are becoming a regular threat to the business community, and it pays to be prepared.
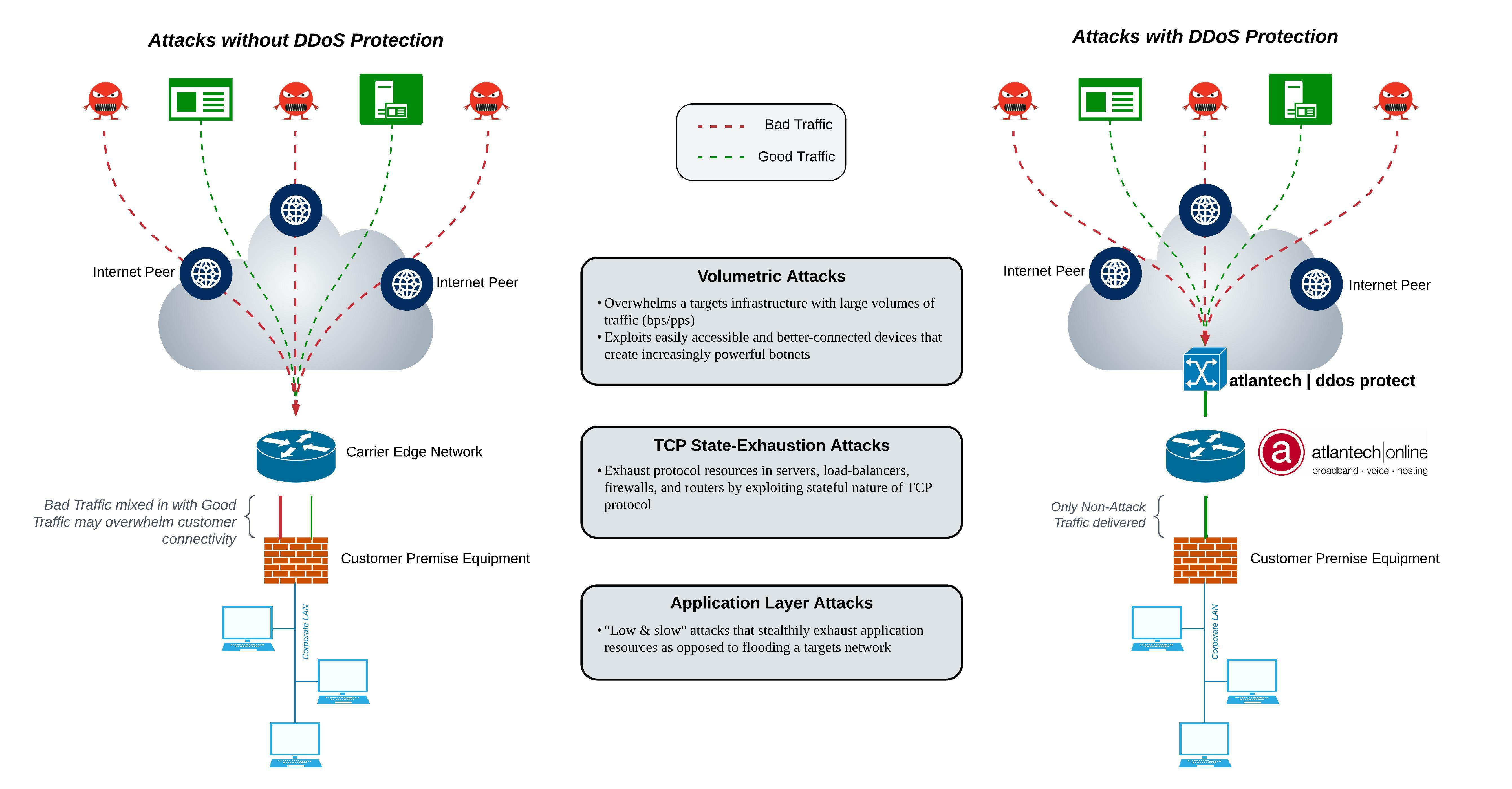
atlantech|ddos protect employs a multi-layered approach to DDoS defense to ensure your organization is safeguarded from both complex, stealthy DDoS attacks, and the very large attacks that can quickly saturate Internet connectivity.
atlantech|ddos protect can deny DDoS attacks at Internet peering points as opposed to inside your LAN at the firewall. If you subscribe to the service, network traffic is constantly analyzed by our NOC. If your network is attacked, an automated alert will notify you that our DDoS protection service is in motion and shielding all your IP address subnets. Bad traffic will be filtered out and only the remaining non-attack related traffic forwarded on to your network equipment.
Among the types of attack that we address are volumetric, reflective and resource-exhaustion. The service is only available with our Dedicated Internet Access services, including those offered in our data centers.
DDoS protection appliances are located at high-volume entry points on the core network where attacks are most likely to occur, such as public transit connections. The appliances automatically inspect all traffic as soon as it arrives at an entry point, immediately discarding malicious packets while sending legitimate packets to their destination. During this process, other network services continue to operate without interruption, even latency- sensitive applications like voice and video.
1. FAST
Any DDoS protection capability needs to be purpose-built for speed and low latency, so attacks are detected and mitigated immediately without impacting network performance. DDoS mitigation is ineffective if it slows your network down to a halt. This defeats the purpose and actually achieves the aims of the intruder!
2. EFFECTIVE
Getting a report after the fact is all well and good. But, you need a solution that can report AND mitigate an attack. Your DDoS protection should be comprehensive, identifying both existing and newly discovered attack types, and preventing direct attacks as well as their side effects. 85% of attacks are less than 10 minutes long. So a manual system is ineffective as it may take at least that long to find out what is going on. An automated response has proven to be most effective.
3. RISK REDUCTION
Kind of like locking the doors on your car or home reduces the risk of a break-in to your property, DDoS protection should provide comprehensive coverage of your public accessible network blocks. Any gaps could increase your risk of an attacker disrupting your business.
4. REAL-TIME FILTERING
Fiber moves data at the speed of light. Voice and video traffic is real time. Make sure the inspection, detection and scrubbing of your data occurs as soon as traffic arrives at your network edge.
5. AUTOMATIC PROCESSING
I've talked to many clients who were disappointed with DDoS service that required manual intervention. A current industry best practice is to have all filtering functions performed automatically, without the requirement for regular human intervention and/or delay.
6. IN-LINE OPERATION
Some cloud DDoS services divert traffic to their scrubbers before passing along to your network. It is ideal for traffic to stay on your network during filtering instead of being physically and/or logically diverted for processing, minimizing latency.
7. COMPREHENSIVE PROTECTION ANALYTICS
Leveraging data collected already enhances the capability to defeat attack vectors. Rapidly updated analytics detect a variety of attack types and are refreshed continually with the latest intelligence on DDoS threats.
8. LAYERED DEFENSE
DDoS protection should be a standard, core function within any company’s security program. DDoS protection should complements existing firewalling, anti-virus, and other security solutions you have already implemented
9. SCALABILITY
Having the ability to scale your DDoS protection service to meet your bandwidth requirements is critical. Just because you have 100 Mbps now, doesn't mean that will always meet your needs. I've had clients go to 10 GigE from 100 Mbps in a matter of months. Make sure your DDoS solution can scale up to meet your bandwidth requirements.
Atlantech Online has been offering cutting-edge communications tools for enterprises in the greater Washington D.C. metro area for over two decades. While best practices have evolved significantly during our years in business, we believe that organizations that pivot to meet customer needs will always win.
With cutting-edge service offerings, such as atlantech|ddos protect, UCaaS and direct connection services such as CloudConnect, Atlantech customers gain the advantage of real-time access to the most advanced business communication tools available today.
To learn how to add DDoS protection to Internet connectivity for your business, please visit atlantech|ddos protect.
Get reliable, blazing-fast internet customized to your bandwidth needs. All backed by our 60-Day “Prove It” Guarantee.

GET IN TOUCH
WHY ATLANTECH
INDUSTRIES
SOLUTIONS
COMPANY
Business Fiber Internet, UCaaS & Phone, and Hosting Services